1. download Office2John
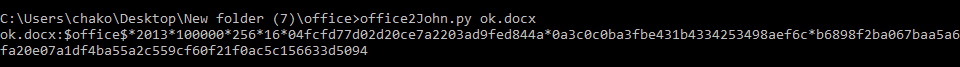
2. run office2john
office2John.py ok.docx
3. download Hashcat
4. run hashcat
we get hashed string from office2john s now we can start to crack it with hashcat
-a, --attack-mode | Num | Attack-mode, see references below
-m, --hash-type | Num | Hash-type, see references below
-i, --increment | | Enable mask increment mode
-1, --custom-charset1 | CS | User-defined charset ?1 | -1 ?l?d?u
-2, --custom-charset2 | CS | User-defined charset ?2 | -2 ?l?d?s
-3, --custom-charset3 | CS | User-defined charset ?3 |
-4, --custom-charset4 | CS | User-defined charset ?4 |
- [ Attack Modes ] -
# | Mode
===+======
0 | Straight
1 | Combination
3 | Brute-force
6 | Hybrid Wordlist + Mask
7 | Hybrid Mask + Wordlist
- [ Built-in Charsets ] -
? | Charset
===+=========
l | abcdefghijklmnopqrstuvwxyz
u | ABCDEFGHIJKLMNOPQRSTUVWXYZ
d | 0123456789
h | 0123456789abcdef
H | 0123456789ABCDEF
s | !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~
a | ?l?u?d?s
b | 0x00 - 0xff
- [ Basic Examples ] -
Attack- | Hash- |
Mode | Type | Example command
==================+=======+==================================================================
Wordlist | $P$ | hashcat -a 0 -m 400 example400.hash example.dict
Wordlist + Rules | MD5 | hashcat -a 0 -m 0 example0.hash example.dict -r rules/best64.rule
Brute-Force | MD5 | hashcat -a 3 -m 0 example0.hash ?a?a?a?a?a?a
Combinator | MD5 | hashcat -a 1 -m 0 example0.hash example.dict example.dict
ex:
hashcat64.exe -a 3 -m 9600 "$office$*2013*100000*256*16*04fcfd77d02d20ce7a2203ad9fed844a*0a3c0c0ba3fbe431b4334253498aef6c*b6898f2ba067baa5a6fa20e07a1df4ba55a2c559cf60f21f0ac5c156633d5094" --force hashcat64.exe -a 3 -m 0 md5.txt -o result.txt ?1?1?1?1?1 -1 ?d --force hashcat64.exe -a 3 -m 9600 hash.txt -o result.txt ?1?1?1?1?1?1?1?1?1 -1 ?l?s hashcat64.exe -a 3 -m 9600 hash.txt -o result.txt ?1?1?1?1?1?1?1?1?2 -1 ?l?s -2 ?l
there are maybe options and hash mode you can choose from
just run hashcat –help then you can see all the options.
you can use hashcat to crack many different has mode/file like md5, pdf,zip,office,wpa/wpa2…etc
easy and short password can easily cracked within mins or even seconds.
Office hash mode options
9700 | MS Office <= 2003 $0/$1, MD5 + RC4 | Documents 9710 | MS Office <= 2003 $0/$1, MD5 + RC4, collider #1 | Documents 9720 | MS Office <= 2003 $0/$1, MD5 + RC4, collider #2 | Documents 9800 | MS Office <= 2003 $3/$4, SHA1 + RC4 | Documents 9810 | MS Office <= 2003 $3, SHA1 + RC4, collider #1 | Documents 9820 | MS Office <= 2003 $3, SHA1 + RC4, collider #2 | Documents 9400 | MS Office 2007 | Documents 9500 | MS Office 2010 | Documents 9600 | MS Office 2013 | Documents
example
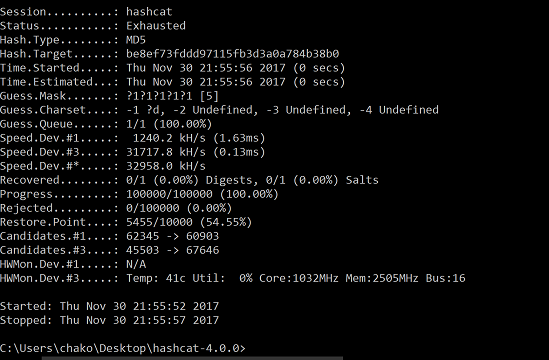
C:\Users\chako\Desktop\hashcat-4.0.0>hashcat64.exe -a 3 -m 0 md5.txt -o result.txt ?1?1?1?1?1 -1 ?d hashcat (v4.0.0) starting... OpenCL Platform #1: Intel(R) Corporation ======================================== * Device #1: Intel(R) HD Graphics 530, skipped. * Device #2: Intel(R) Core(TM) i7-6700HQ CPU @ 2.60GHz, skipped. OpenCL Platform #2: NVIDIA Corporation ====================================== * Device #3: GeForce GTX 960M, 512/2048 MB allocatable, 5MCU Hashes: 1 digests; 1 unique digests, 1 unique salts Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates Applicable optimizers: * Zero-Byte * Early-Skip * Not-Salted * Not-Iterated * Single-Hash * Single-Salt * Brute-Force * Raw-Hash Password length minimum: 0 Password length maximum: 256 Watchdog: Temperature abort trigger set to 90c Watchdog: Temperature retain trigger disabled. Approaching final keyspace - workload adjusted. Session..........: hashcat Status...........: Cracked Hash.Type........: MD5 Hash.Target......: 827ccb0eea8a706c4c34a16891f84e7b Time.Started.....: Sat Nov 18 03:37:08 2017 (0 secs) Time.Estimated...: Sat Nov 18 03:37:08 2017 (0 secs) Guess.Mask.......: ?1?1?1?1?1 [5] Guess.Charset....: -1 ?d, -2 Undefined, -3 Undefined, -4 Undefined Guess.Queue......: 1/1 (100.00%) Speed.Dev.#3.....: 93590.8 kH/s (0.23ms) Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts Progress.........: 50000/100000 (50.00%) Rejected.........: 0/50000 (0.00%) Restore.Point....: 0/10000 (0.00%) Candidates.#3....: 12345 -> 97646 HWMon.Dev.#3.....: Temp: 43c Util: 26% Core:1032MHz Mem:2505MHz Bus:16 Started: Sat Nov 18 03:37:03 2017 Stopped: Sat Nov 18 03:37:10 2017 C:\Users\chako\Desktop\hashcat-4.0.0>